Fine-grained, scalable authorization in minutes
Resource-level access controls for any application, managed centrally and evaluated instantly.


Fast

~1ms authorizations

Flexible

Any model, any cloud

Easy

Get started in <5 minutes
Watch a 2-minute video
Granular permissions, live in minutes
Use our SDKs, quickstarts, and sample apps to easily integrate the Aserto fine-grained authorization platform.
Roles, hierarchies, subscriptions, sharing & collaboration, ready-to-go in minutes.
const { jwtAuthz } = require("@aserto/aserto-node")
const checkAuthz = jwtAuthz({ ... })
// ...
app.get("/protectPath/:param", checkJwt, checkAuthz,
async (req, res) => { ... }
)
Node

Go

Python

Java

.NET

Ruby
Real-time authorization
Eliminate standing permissions. Enforce in milliseconds, based on real-time data.
Deploy local authorizers to the edge of your application and let Aserto do the rest. The Aserto control plane will sync changes to authorization data with them in real-time to ensure you never authorize over stale data.
Central control
Manage all of your users, policies, authorizers, and authorization data from one place.
The Aserto control plane makes understanding authorization logic and managing access across applications as easy as pie.
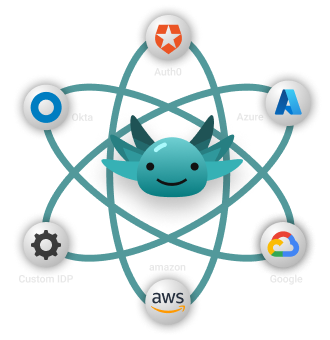
Works with what you have
Seamlessly add authorization to any application using our complete set of SDKs middleware, or using our gRPC / REST APIs. Then connect your identity provider, user directory, and SIEM tools using our pre-build integration.

Zero trust and least privilege by default
There is no zero trust without fine-grained access controls. Ensure users can only access what they need to at the moment, and easily change that logic, or what they can access.
allowed {
ns := time.now_ns()
day := time.weekday(ns)
day == data.workdays[_]
}allowed {
input.user.properties.dept == "Sales"
}allowed {
ds.check({
"subject_type": "user",
"subject_id": input.user.id,
"relation": "manager",
"object_type": "user",
"object_id": input.resource.id
})
}allowed {
ds.check({
"subject_type": "user",
"subject_id": input.user.id,
"relation": "can_read",
"object_type": "document",
"object_id": input.resource.id
})
}allowed {
ns := time.now_ns()
day := time.weekday(ns)
day == data.workdays[_]
}allowed {
input.user.properties.dept == "Sales"
}allowed {
ds.check({
"subject_type": "user",
"subject_id": input.user.id,
"relation": "manager",
"object_type": "user",
"object_id": input.resource.id
})
}allowed {
ds.check({
"subject_type": "user",
"subject_id": input.user.id,
"relation": "can_read",
"object_type": "document",
"object_id": input.resource.id
})
}allowed {
ns := time.now_ns()
day := time.weekday(ns)
day == data.workdays[_]
}Compliance without the headache
Aserto automatically collects and aggregates authorization decisions along with all of the inputs, so you have complete audit trails. You can even map decisions to policy versions and the data that was used.
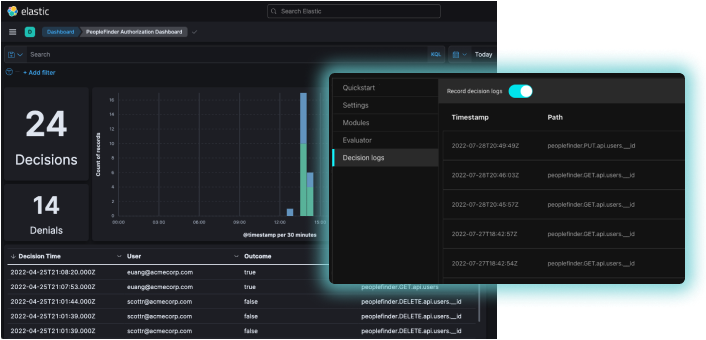
Cloud-native and open source
Aserto is based on a modern, cloud-native, open-source foundation, including the Topaz open-source authorizer, Open Policy Agent decision engine, and a Google Zanzibar inspired directory.

Don't build undifferentiated plumbing
Authorization is complex
Evaluating policy against real-time user attributes with millisecond latency and 100% availability is a distributed systems problem. Most engineering teams can’t justify taking the time to fully solve it.
Requirements constantly evolve
Custom roles. Custom attributes. Integration with enterprise identity providers and directories. Decision logs. ISO 27001. As products move up-market, teams that build them can't keep up.
You could be building customer value
"I want to rewrite RBAC!" said no engineer, ever. Your team could be working on end-user features instead of undifferentiated heavy lifting.
Built by developers, for developers


Sam Hall
Head of Technology, Metrikus
"Authorization has been a constant worry over the last two years - everyone was scared of it. With Aserto, I'm so much more comfortable with authorization because I can see what's going on. Before, it was a dark art - we had a muddled permission structure. With Aserto, we have clear policies that are easy to implement and obvious to analyze. Aserto has made AuthZ something we're not scared of anymore."


James Lindenbaum
Founder, Heroku & Heavybit
“A policy-centric authorization solution for developers is a glaring hole in the market, and there is no team on the planet better equipped to build it to enterprise-grade."


Grant Miller
Co-founder / CEO, Replicated
"B2B SaaS vendors have a huge opportunity going after the enterprise, but only if they meet enterprise expectations, as we've captured in EnterpriseReady.io. Replicated serves 50% of the F100, and we know first-hand that authorization and RBAC are table-stakes for enterprise adoption. It's obvious to me that partnering with Aserto is a far better approach compared to rolling your own and having to reinvent the wheel."


David Kerber
VP of Technology
"Authorization involves really hard problems that I want experts to solve. We like to focus our internal engineering efforts on our customers and their problems. Aserto allows us to do just that, at a small fraction of the cost it would take to build and maintain it ourselves, not to mention the opportunity cost."


Mathias Biilmann Christensen
Co-founder & CEO, Netlify
"As millions of developers and businesses are adopting a Jamstack approach, most modern web applications involve multiple APIs and services. Aserto's promise of separating policies from code could radically simplify the implementation of authorization across the front-end UI and the larger world of back-end functions and endpoints."


Tom Preston-Werner
Co-founder, GitHub
"Building & managing an authorization/RBAC system is a huge pain, especially at enterprise scale. So stop! Aserto has a distributed, millisecond latency, 100% availability API for that. I'm excited to help as an angel investor!"


Sam Hall
Head of Technology, Metrikus
"Authorization has been a constant worry over the last two years - everyone was scared of it. With Aserto, I'm so much more comfortable with authorization because I can see what's going on. Before, it was a dark art - we had a muddled permission structure. With Aserto, we have clear policies that are easy to implement and obvious to analyze. Aserto has made AuthZ something we're not scared of anymore."


James Lindenbaum
Founder, Heroku & Heavybit
“A policy-centric authorization solution for developers is a glaring hole in the market, and there is no team on the planet better equipped to build it to enterprise-grade."


Grant Miller
Co-founder / CEO, Replicated
"B2B SaaS vendors have a huge opportunity going after the enterprise, but only if they meet enterprise expectations, as we've captured in EnterpriseReady.io. Replicated serves 50% of the F100, and we know first-hand that authorization and RBAC are table-stakes for enterprise adoption. It's obvious to me that partnering with Aserto is a far better approach compared to rolling your own and having to reinvent the wheel."


David Kerber
VP of Technology
"Authorization involves really hard problems that I want experts to solve. We like to focus our internal engineering efforts on our customers and their problems. Aserto allows us to do just that, at a small fraction of the cost it would take to build and maintain it ourselves, not to mention the opportunity cost."


Mathias Biilmann Christensen
Co-founder & CEO, Netlify
"As millions of developers and businesses are adopting a Jamstack approach, most modern web applications involve multiple APIs and services. Aserto's promise of separating policies from code could radically simplify the implementation of authorization across the front-end UI and the larger world of back-end functions and endpoints."


Tom Preston-Werner
Co-founder, GitHub
"Building & managing an authorization/RBAC system is a huge pain, especially at enterprise scale. So stop! Aserto has a distributed, millisecond latency, 100% availability API for that. I'm excited to help as an angel investor!"


Sam Hall
Head of Technology, Metrikus
"Authorization has been a constant worry over the last two years - everyone was scared of it. With Aserto, I'm so much more comfortable with authorization because I can see what's going on. Before, it was a dark art - we had a muddled permission structure. With Aserto, we have clear policies that are easy to implement and obvious to analyze. Aserto has made AuthZ something we're not scared of anymore."


James Lindenbaum
Founder, Heroku & Heavybit
“A policy-centric authorization solution for developers is a glaring hole in the market, and there is no team on the planet better equipped to build it to enterprise-grade."


Grant Miller
Co-founder / CEO, Replicated
"B2B SaaS vendors have a huge opportunity going after the enterprise, but only if they meet enterprise expectations, as we've captured in EnterpriseReady.io. Replicated serves 50% of the F100, and we know first-hand that authorization and RBAC are table-stakes for enterprise adoption. It's obvious to me that partnering with Aserto is a far better approach compared to rolling your own and having to reinvent the wheel."



Join our slack
Discuss authorization patterns, get answers, and engage with our community.

Sign up for our newsletter
Get the latest technology articles and company updates in your inbox.

&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)